Information Security
Information security (cybersecurity) is the state of security of electronic information resources, information systems and information and communication infrastructure from external and internal threats.
Information security includes strategies, methods and processes for protecting information and IT assets from unauthorized access and risks that may violate the confidentiality, integrity or availability of information.
Corporate security extends to the security of data transmitted over a connected network, servers and end users. It covers technologies, people and processes related to maintaining a secure environment for digital assets, additionally focuses on regulatory requirements for the protection of assets and data owned by an organization.
Ensuring the security of cyberspace and protecting the information and communication infrastructure is the most important task of the state in the modern digital world. That is why information security is an integral part of national security. On behalf of the First President of the Republic of Kazakhstan, the implementation of the Cybersecurity Concept “Cyber Shield of Kazakhstan” has been launched in the country since 2017.
How is Cybersecurity Ensured in the Fund Group of Companies
According to legislative requirements of the Republic of Kazakhstan, one of the directions of the Fund operational activities is to ensure information security of the Fund information and communication infrastructure, as well as coordination of information security subdivisions of Portfolio Companies of the Fund.
The main objectives of the Fund in this field of activity are to ensure the availability, integrity, confidentiality and fault tolerance of information.
Achieving these goals is possible through the implementation of the following tasks:
Firstly, it is the creation of a legal framework for the formation of a unified policy in the field of information security of both the Fund itself and its portfolio, subsidiaries and dependent organizations with the support of appropriate monitoring.
Secondly, ensuring the information security of the Fund and coordinating the activities of this area in all its structures.
Operational Information Security Center of the Fund
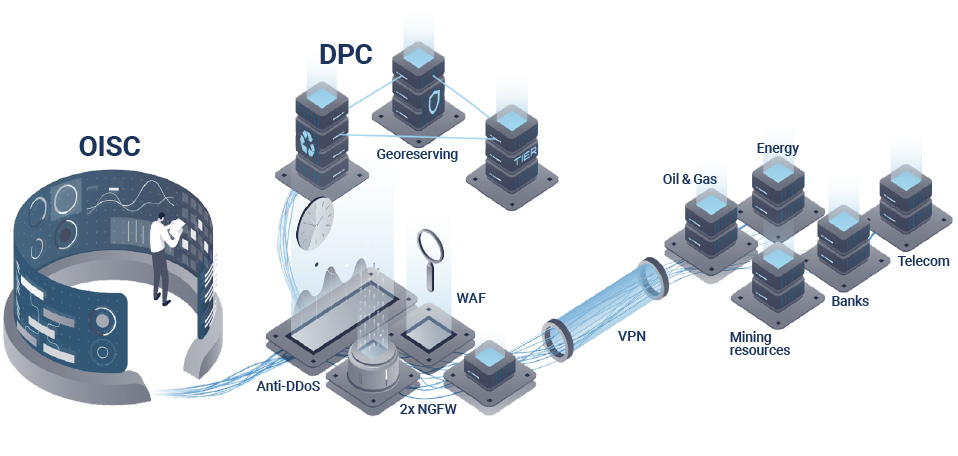
The regulation and management of coordinating the business of Portfolio Companies, subsidiaries and dependent organizations is carried out according to the Corporate Information Security Standard approved by the decision of the Management Board of the Fund.
The protection of the external perimeter and monitoring of the analysis of information security events of the Fund group of companies are provided based on the operational information security center of QazCloud LLP.
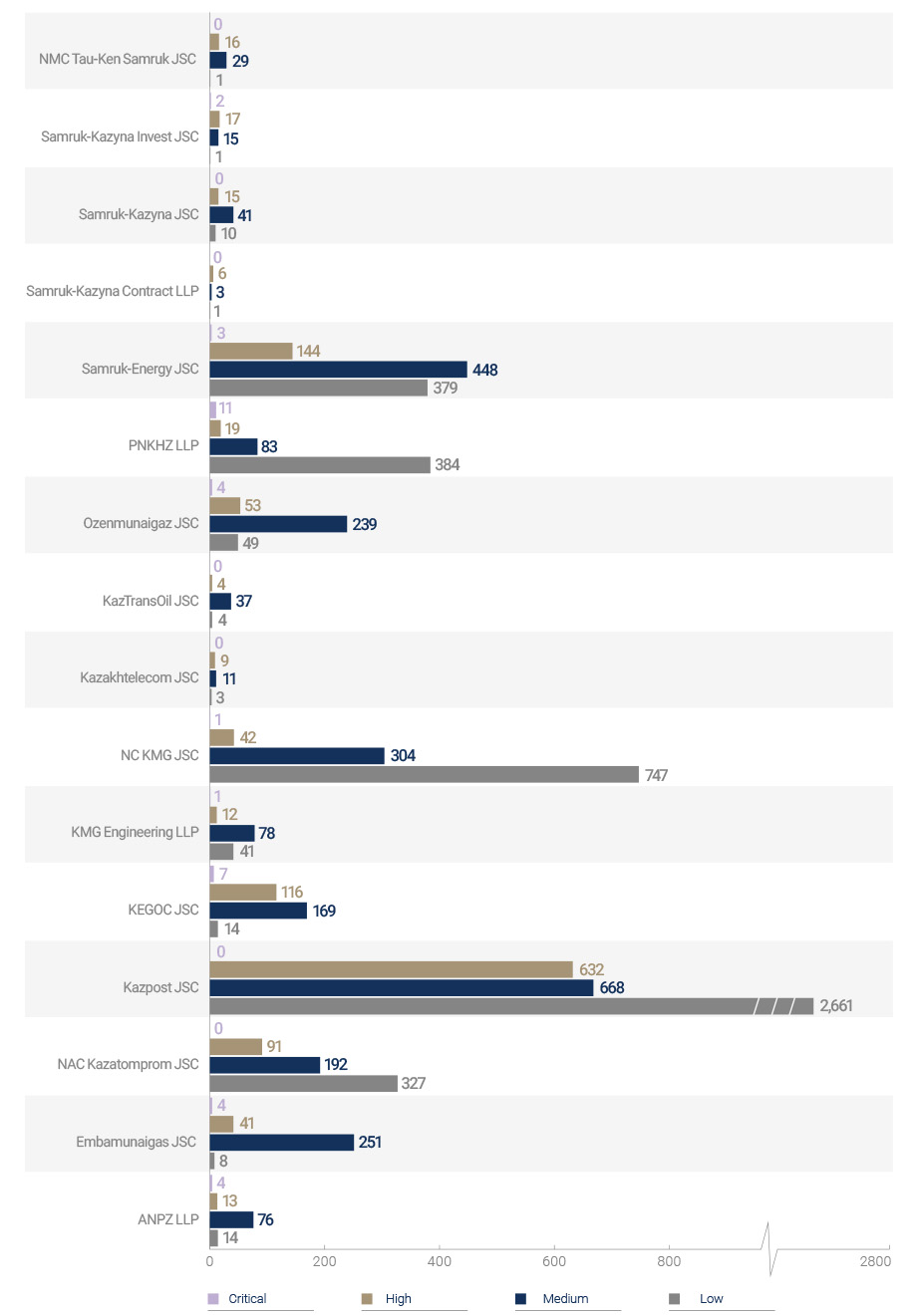
Four information security audits of the IT infrastructure of Portfolio Companies, subsidiaries and dependent organizations were held in 2022.
In total, 38 critical incidents were identified in the Fund group in 2022, for which investigations were held with the participation of digital forensics specialists and measures were taken to protect the IT infrastructure.
Solving these issues will ensure a continuous process of improving and analyzing the security of the IT infrastructure of the Fund Group.
Considering the trend of cyber threats, the Fund has begun to develop the Information Security Development and Provision Strategy for 2023-2027.
As part of the Strategy, it is planned to form a set of specific actions to counter cyber threats in the Fund and ensure the information security of its Portfolio Companies, plan the purchase of appropriate software, develop information security requirements, motivate employees to strictly comply with the norms of corporate culture and ensure cyber hygiene.
However, for the effectiveness of activities in this direction, it is necessary to solve a number of issues that are a condition for creating the Strategy.
First, to form a unified information security architecture for the entire group of the Fund companies. Secondly, it is necessary to focus on improving the level of information security in the Fund, including critical information and communication infrastructure facilities. Thirdly, to implement the requirements of the international standard ISO/IEC 27001 27001 in the Fund, followed by obtaining the appropriate certificate
Solving these issues will ensure a continuous process of improving and analyzing the security of the IT infrastructure of the Fund group.
Incident statistics for 2022 in the Fund group
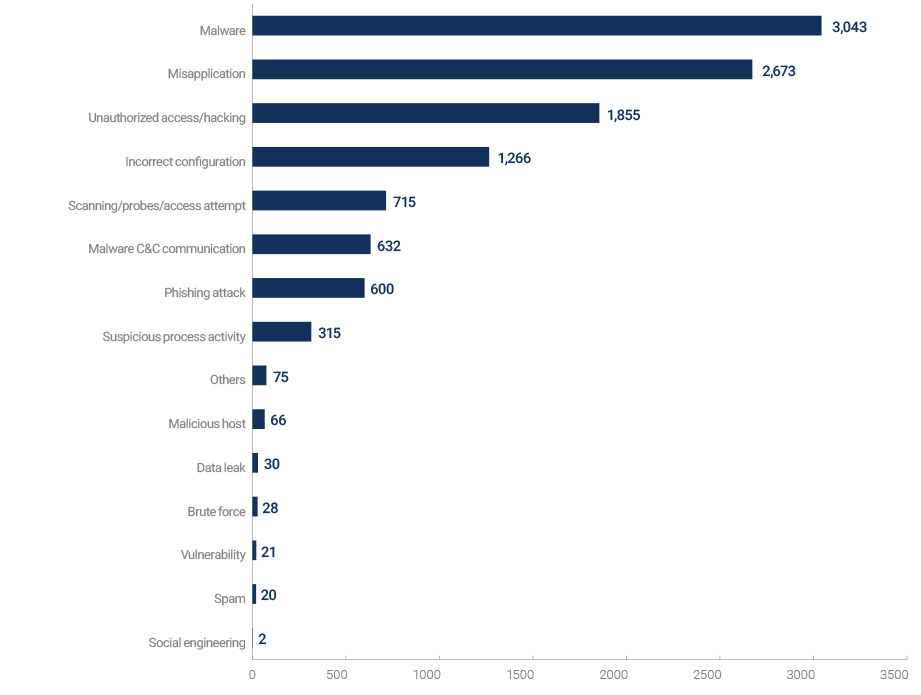
Incident statistics by threat types for 2022 in the Fund group